IIOT: Remote access platform for IoT devices
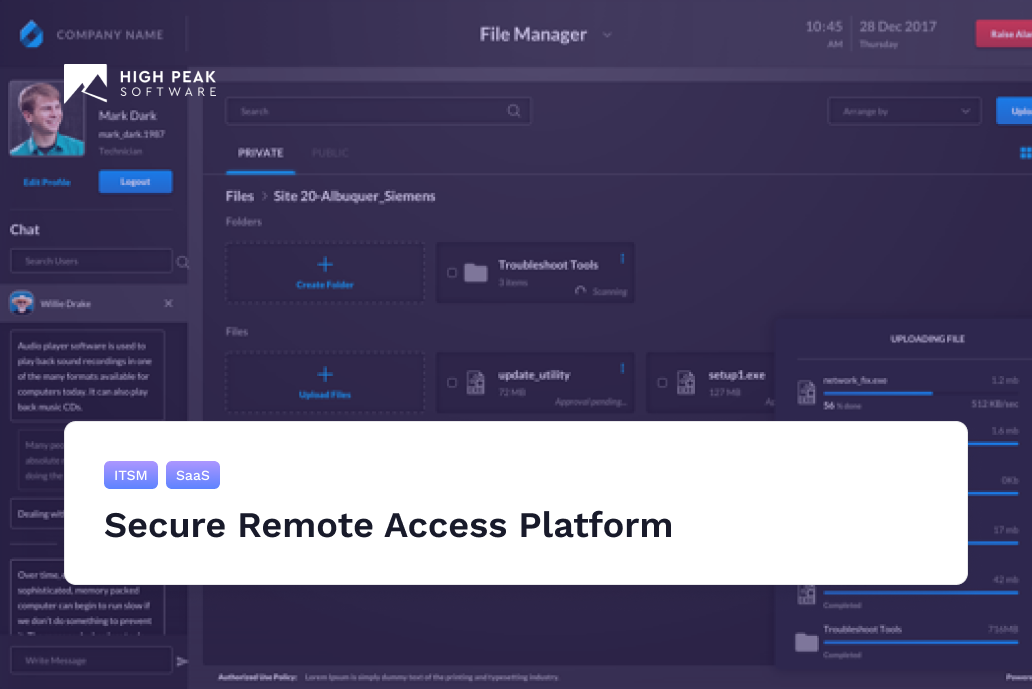
Table of Contents
- Building IIOT
- Why did High Peak see the need to create IIOT?
- Challenges faced by High Peak while creating this IoT device
- IIOT: High Peak Software’s solution for remote access
- Technologies leveraged by IIOT
- Planning to build an impactful product and quickly take it to market? Let’s talk!
Building IIOT
IIOT is High Peak Software’s advanced solution for remote access. The software helps you access, control, and monitor remote systems virtually anywhere in the world. It’s beneficial for working with any remote system, including IoT assets.
Most organizations use systems remotely, given the nature of their operations, but providing secure access has always been a concern. We built the software intending to help enterprises take back control of their remote systems. Considering that activities related to accessing and securing these systems lead to too many overhead costs, we’ve designed software to make the process smoother and more efficient.
IIOT consists of three user roles: Global admin, Site admin, and Technician.
Based on the role, users are provided varying access levels to the remote systems—a much-needed utility. The privilege role-based access feature is an excellent addition for organizations that have to deal with too many stakeholders for one operation.
IIOT was a creation for keeping a remote user in mind, which means that any industry that employs such devices for operational purposes would stand to benefit from it. Some of them include Oil and Gas, Manufacturing, Energy, Information Technology (IT), Smart cities & countries, etc.
Why did High Peak see the need to create IIOT?
In highly technical industries such as Oil & Gas, Manufacturing, Robotics, etc., it’s prevalent to use remote devices to monitor systems. The problem with that is that most of these plants are based in remote or distant areas. It means that the presence of an on-site technician is not mandatory. During remote device deployment, having an individual monitor its activities defeats the purpose of using remote devices. It negates the advantages they offer.
Devices that require repair or maintenance will need on-site attention from technician teams. They must travel to the location of the deployed devices to perform the necessary work. Extreme weather changes and limited access to plants or remote areas can make device access difficult. Remote access software can help address these issues, improving efficiency and reducing costs.
There are many costs associated with on-site repairs or maintenance. For example, travel expenses, equipment costs, and labor costs for personnel. These expenses can add up quickly. Remote access to devices in remote locations allows for damage assessment without sending repair teams on-site. Thus, improving efficiency and reducing costs. This can save time and money by identifying problems before mobilizing resources. It can also lead to faster issue resolution. This would save them time and effort in the assessment stage. Ultimately, helping them spend more time fixing the problem.
The goal is to help operators access their remote devices in a secure, safe, and efficient manner—which is why we created IIOT.
Challenges faced by High Peak while creating this IoT device
Given the needs of the ideal user in mind, High Peak Software’s engineering team identified three key issues to resolve: Remote access to devices, Enabling real-time communication, and Maintaining security standards. Let’s dive into what that means for you.
Poor device accessibility
We know that access is an issue, but it could mean a lot more than that for field engineers. More often than not, they need to travel to relatively inaccessible places to repair the organization’s devices and network. Even when remote monitoring is enabled, they are unable to access specific parts of the network or cannot collaborate with other users—making it tedious to complete the job.
Real-time communication
Real-time communication has always been a concern in this domain because of the lack of connectivity. When you’re monitoring devices, it’s crucial to have a continuous feedback process coupled with an open line of communication as it helps in dealing with issues as and when they happen. It leaves no room for downtime, but that’s not always the case.
Security concerns
Any system present on a virtual network is prone to vulnerabilities, and remote devices are no different. When it comes to accessing these devices, three issues need to be considered:
- Providing privileged based access
- Preventing security breach
- Preventing malware attacks
Only when these aspects are accounted for can the entire organization access their remote devices securely.
Now that we understand what challenges High Peak Software was looking to solve let’s dive into how we’ve done it.
IIOT: High Peak Software’s solution for remote access
IIOT makes it possible for organizations to consolidate all their remote devices and manage them on one dashboard. On this dashboard, the stakeholders within the organization can provide access and monitor usage and potential breaches whenever they need to.
The users can set up their systems and access relevant data while being able to assign time-sensitive roles for different projects on an as-needed basis. They can perform all these activities right from the comfort of their home or workplace without any hassles.
Below, we’ve detailed the core features of the IIOT platform and how it can benefit you.
Privilege role-based access
On the IIOT platform, there are three kinds of user roles:
- Global admin
- Site admin
- Technician
Considering that not every user needs to have access to all the platform assets, these roles can be assigned depending on what they need for the job. For example, if a repair job is pending for an oil rig, the admin responsible for the maintenance team would be the ‘Global admin,’ the on-site manager would be the ‘Site admin,’ and the technician assigned for the maintenance job would be the ‘Technician.’
Global admin role
The Global admin has access to everything on the platform. They are responsible for setting up the organization because they are offered complete capabilities. The admin can add and remove users, provide and revoke access as needed and are also responsible for approving the storage/ delivery of any files deposited in the database. They are the user admin, asset admin, and configurations admin, too, and any issues arising concerning IIOT’s usage will have to be raised with them.
They can either create it on the platform or import a Microsoft Excel sheet with all the user information to add users. Once all the details are added, users receive their login link via email, and they’re good to go.
Site admin role
Site admin can also help create and onboard users but do not have the complete capabilities offered by the platform. They also have functionalities such as adding or importing assets, setting up specifics such as session duration, number of sessions, protocols, asset classifications, etc. and accepting or denying file upload and storage requests.
Technicians
Technicians, on the other hand, have minimal capabilities. Only when they are permitted by Site or Global admin to access these devices can they do so. They can also upload and send files that need to be approved by the admins. They can only access one session at a time, and they need to specify how long they need to do it. All in all, admins can control access at a very minute level which ensures that unauthorized personnel can’t access the platform and linked devices.
Asset management
When it comes to asset management, any assets that need to be logged onto the platform will fall under two categories: Asset classes and Asset groups. Asset classes are based on the vendor or device, whereas Asset groups are based on where these devices are located. For example, if your organization has two branches—Branch X and Branch Y—these form a part of asset groups. But, if your organization is using two devices—Device A and Device B—they form a part of asset classes.
The assets are classified to ensure that users receive access to a particular set of assets only, thereby enabling control over them. Depending on how the assets intersect, access is provided to Site admins or Technicians.
Repository: Storage & archives
Devices can only be linked once they can be detected by the platform, which is why having a file database is useful. For example, suppose the Technician is trying to fix an internal issue in a remote device. They can send the necessary files through IIOT, which can then be downloaded for various purposes.
Uploaded files need to be malware-free, so the platform scans them for viruses before uploading them. Once it’s uploaded, the admins can accept or deny its storage on the software—maintaining the integrity of the database. If accepted, it enters the public repository and can be viewed by those who access these files. These files can be sent during the session or uploaded before it.
The platform also gives users the option to store, access, and archive the files—like any other database. If a particular folder exceeds the storage limit, automation can be set up to archive them when they do.
Continuous monitoring
At any given point in time, the admins can monitor how many users are active on the platform, which users have access to specific assets, and how many sessions are ongoing. It gives them complete control of how the devices are accessed, and in the case of any breach, they can immediately identify them—kill those sessions—and revoke access.
This feature is handy for organizations where it’s common to have multiple stakeholders on the platform, including third-party vendors. Using privileged role-based access, they can protect assets while enabling technicians to do their job with what they need.
Also, the platform allows integrations as well. If the user has logged in previously and the admins want to create a role for them, their details are pulled automatically. At any given point in time, admins can also generate reports based on usage, role, and audit logs, which help continuously monitor all the assets and users.
Secure communication
A huge part of enabling secure remote access is that every potential vulnerability has to be accounted for—which is what IIOT does. For example, when new users are uploaded or created on the platform, they are sent a link via email to log in (single sign-on) securely. After that, they can create passwords for their accounts, but the major distinction is that the Global admin can control the types of passwords created. It means that they can specify how many numbers, letters, or other characters are required to create one. Also, if the user wants the option for SSO authentication every time they log in, they can enable that too, increasing security.
Users can also participate in real-time chats with other users, which helps keep the line of communication open. They can not only chat but transfer necessary files relevant to the purpose of the task and raise alarms if they run into any problem or any suspicious activity is noticed. When alarms are raised, they are directly sent to the admins, who manually review the issue and rectify it. All these actions are recorded with timestamps on the audit logs—ready to be accessed anytime.
Technologies leveraged by IIOT
- Backend: Java, Spring Boot, Hibernate, MySQL, Guacamole server, Clam AV, Redis, Elastic Search
- Frontend: React, Redux, Redux Sagas, React Router, Graylog, Cloudwatch
- DevOps: Docker, Docker Swarm, Kubernetes, Prometheus, Grafana, Nginx, Jenkins, Ec2, S3, ELB, EFS, RDS


